
Definition: Security has a very important role to play in any ERP implementation. The security aspect of an ERP helps the administrator to restrict the data to the users and provides enough rights to the user as per the roles and responsibilities (department). The security administrator can control the rights of access to different Modules, Forms, reports based on the User group or individual user.
A security role represents a behavior pattern that a person in the organization can play. A security role includes one or more duties.
A duty is a responsibility to perform one or more tasks. A duty includes one or more privileges.
Duties are a group of related privileges required to perform a task
- Maintain bank related transaction
- General deposit slips
- Cancellation of Payment
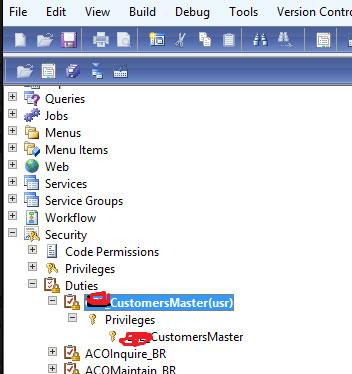
Privileges specify the access that is required to perform a duty. A privilege includes one or more permissions.
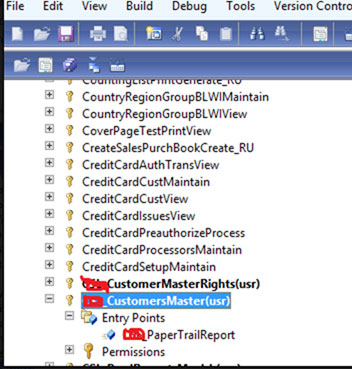
Privileges specify the access that is required to perform a duty. A privilege includes one or more permissions i.e. we can more than one entry points by simply drag and drop functionality based on the menu item. And you can set the access level on the entry points permission properties as No Access, read, update, create, correct, and delete. Delete the highest permission level.
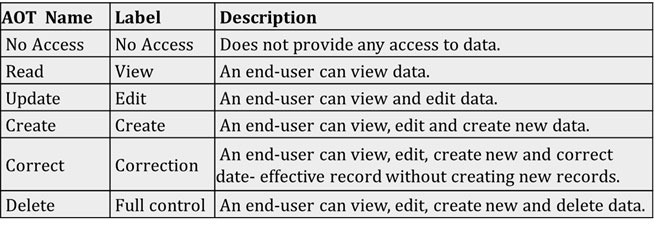
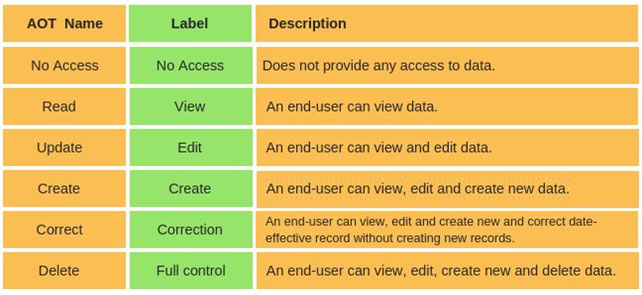
Access levels
No Access - No Access to data
Read - User can View Data
Update - User can View and Edit Data
Create - User can View, Edit and Create new Data
Correct - User can View, Edit, Create new and correct date-effective records without creating new records.
Delete -User can View, Edit, Create new and Delete Data
Roles:-
Now we have to create roles and drag duties earlier we have created under the Duties node.
All of the users must be assigned at least one security role to have access to Microsoft Dynamics AX. By managing the user’s access through security roles.

Permissions:
Include the access level to one or more securable objects that are required to perform the function associated with an entry point.
Once security role must be assigned to all the users to access the Axapta, based on security roles that are assigned to the user determine the duties that user can perform, and depending on that limited interface user can view
Purpose of security : -
- System will be more secure. User can access their respected module. He will not enter into the other module.
- Data will be safe and secure. No other user has to delete any record in ax 2012.
Security – Standard Operating Procedure (Policy, Process, Roles, and Audit)
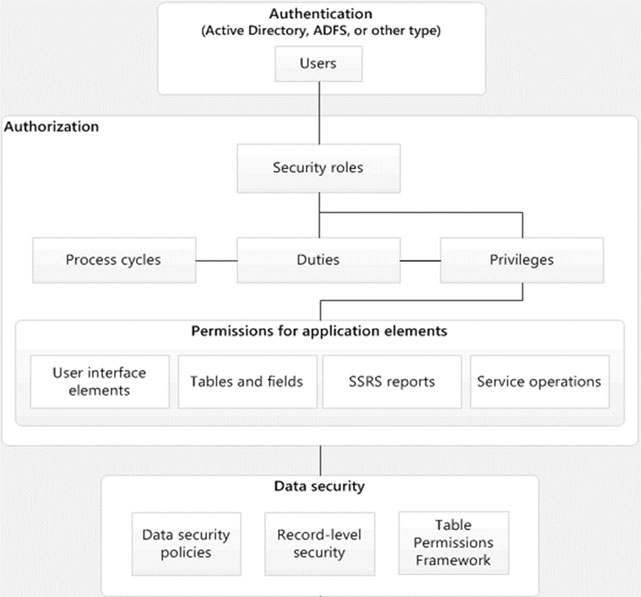
Security Architecture of Microsoft Dynamic AX 2012
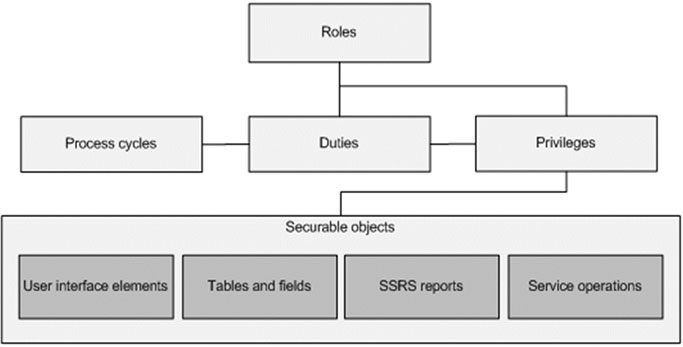
Role Based Security Concepts
More about Security
Security Roles: All users must be assigned to at least one security role to have access to Microsoft Dynamics AX. Roles combine multiple Duties to allow a user to perform the multiple processes necessary to perform their specified day job. Users are assigned to one or more security roles.
Duty: A Duty combines multiple privileges to provide a user with the appropriate access to perform a specific process within AX. Duties are designed with a specific business objective in mind.
Privileges: Specify the access that is required to perform a duty. A privilege contains permissions to individual application objects, such as user interface elements and tables. It is essential to apply the principle of least privilege, granting only the minimum necessary permissions needed to complete the task. Privileges group together related securable objects. For example, menu items and controls.
Privileges can be assigned directly to roles. However, for easier maintenance, we recommend only assigning duties to roles.
Entry Point: An entry point is the object that triggers a user action to start a particular function, such as a form or a service.
In Microsoft Dynamics AX, there are three different types of entry points - menu items, Web content items, and service operations.
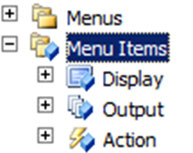
Type of Menu Item
Menu item:- Object of the form.
Three type of Menu Item.
- Display
- Output
- Action
Role Based Security Concepts
Output: Objects which are primarily for presenting data to the user such as forms and dialogs.
Display: An output menu item should have the sole purpose to print a result.
Action : If your runnable object has an action to perform, for example creating or updating data
Permission
Include the access level to one or more Securable objects that are required to perform the function associated with an entry point. This could include any tables, fields, forms, or server-side methods that are accessible through the entry point.
There are Six type of permission:
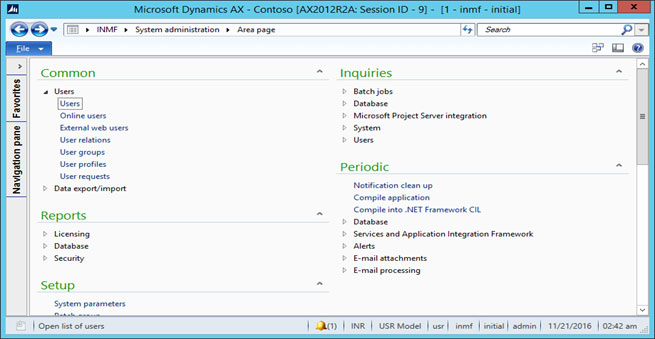
Path: System administration > Users > Users
This is the path where all the users are defined in the ax 2012.
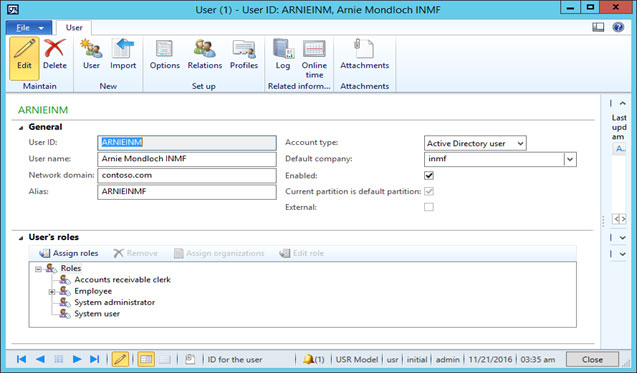
• Select user name and edit.

• Assign the roles to user

• Assign the roles to user
• Open the desired form, which you want to give the access on it (Here I have used the purchase order form).
• Find object name, right click on object and Select Personalize.
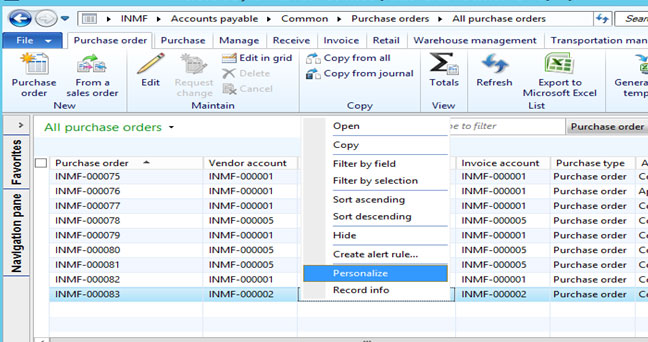
• Check the form name and menu item in Information tab.
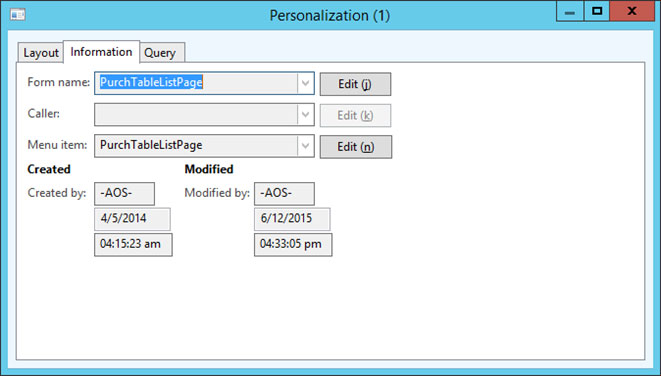
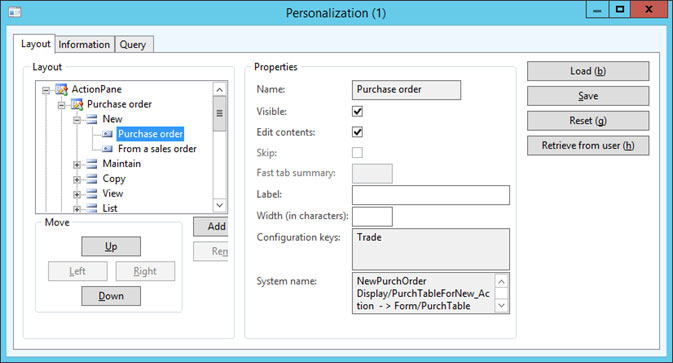
• Check Button name in System Name “PurchTableForNew_Action”
• Open AOT option for create privilege and roles, shortcut key is ctrl+D.
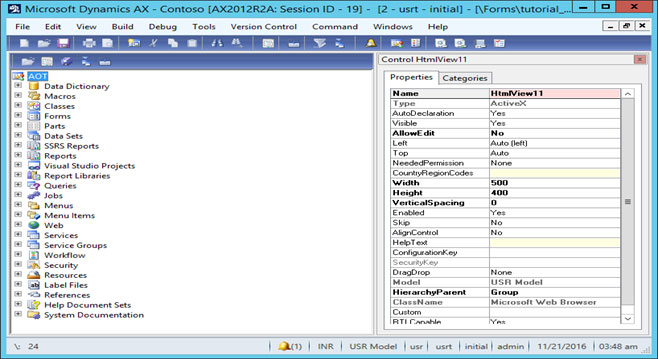
• Security > Privilege > New Privilege
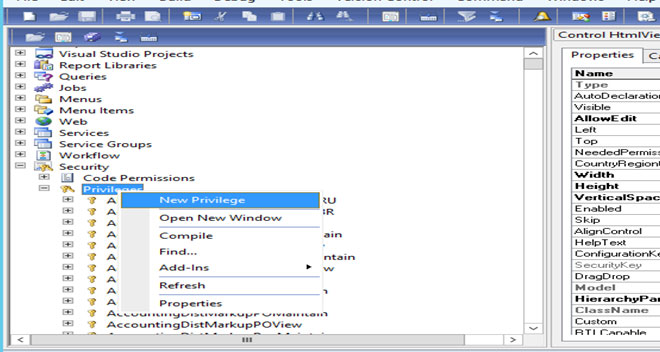
• Right click on Entry point and create new entry point.
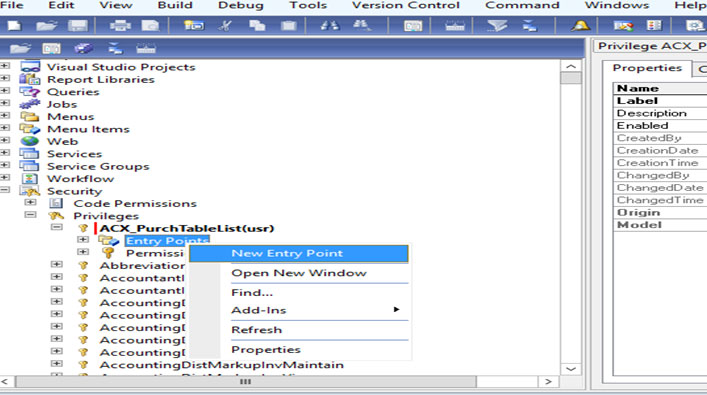
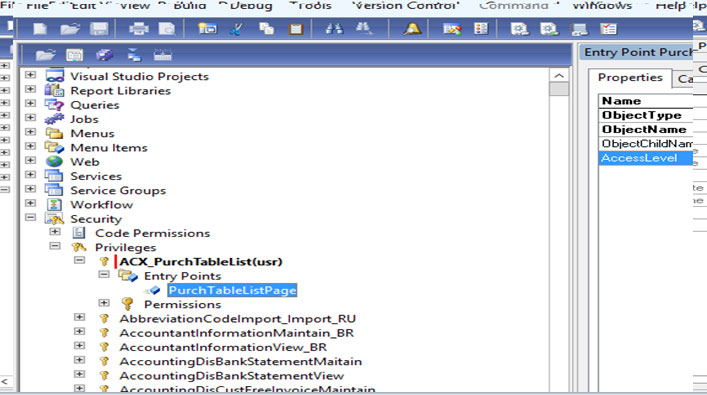
• Click on entry point for display the property
• Fill the following information in Entry point property
• Security > Roles > New Roles
• Right click on Roles and create new role.
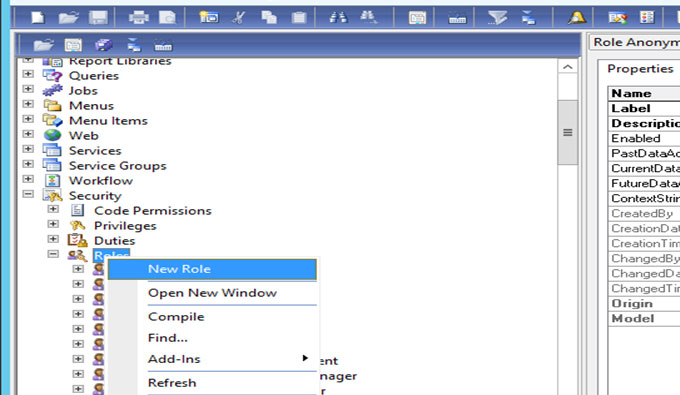
• Open privilege option and create new privilege in roles
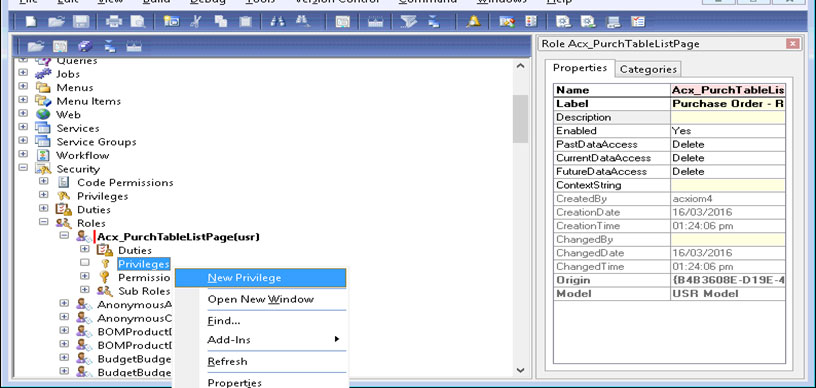
• Already created privilege name select so its link
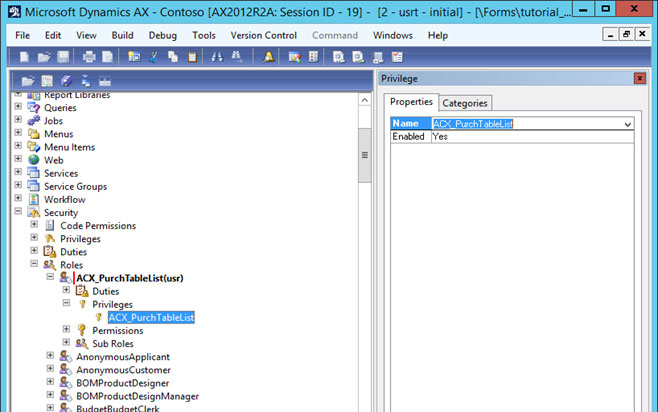
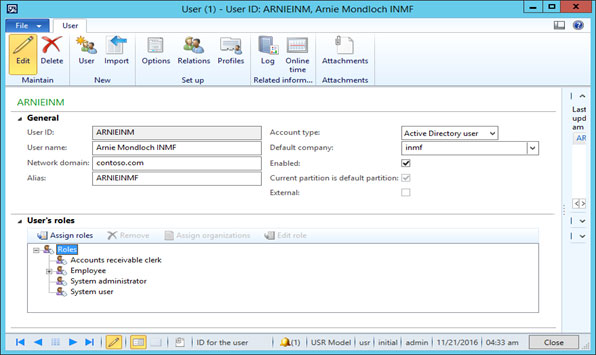
• Click on Assign Roles for add the roles
• Below form will be open, search role name from list and click on OK
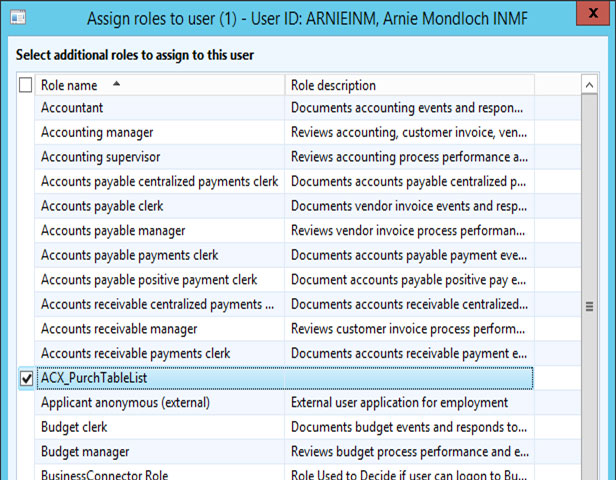
Purchase Order role add in list
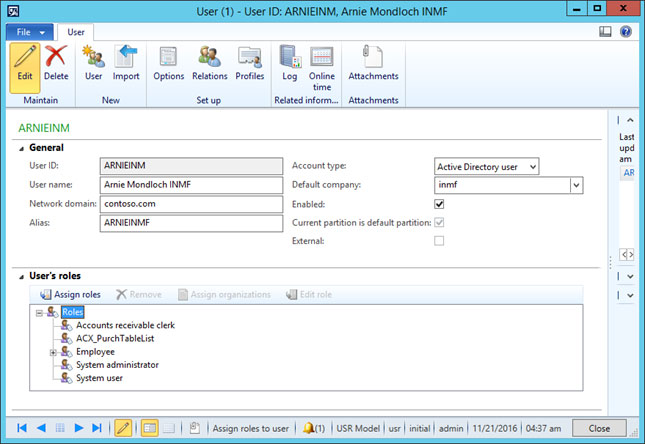
This user has only purchase order display access
Conclusion
In the end, Suppose the user has the rights of creating purchase order only, So when the user has to open the purchase order he can see the only one module that is an account payable, in that module he has only rights to create purchase order only. He will see only the purchase order list form where he can create, delete or edit the purchase order, and also he cannot see the other module also.
The purpose of the security is that user has their right he can see only the respected modules which they want to work on. So that our Axapta will be more secure after providing security.
This blog is written by a team of Dynamics AX senior developers from NEX Softsys, you can ask any question related to dynamics AX. Our Microsoft Dynamics AX consulting provide expert advice for a various business sector like Industries, Health care, Logistics & other well-known industries.



